Challenge Scenario
Description: In this challenge, we're provided with a memory dump (.mem) and an instance in order to solve 8 questions and retrieve the flag. We're tasked with investigating a phishing incident where a malicious email attachment compromised a system.
Initial Setup
Forensics Tool: Volatility 3
Since we have a memory dump, we'll use Volatility 3 for our analysis. Volatility is the industry-standard framework for memory forensics, allowing us to extract processes, files, registry keys, and other artifacts from memory dumps.
Analysis Type: Windows Memory Forensics
Goal: Trace the complete attack chain from email delivery to persistence
Question-by-Question Analysis
Question 1: Process Used to Deliver Malicious Attachment
Question: What process was used to deliver the malicious attachment?
We start by enumerating all running processes in the memory dump using Volatility's windows.pslist plugin:
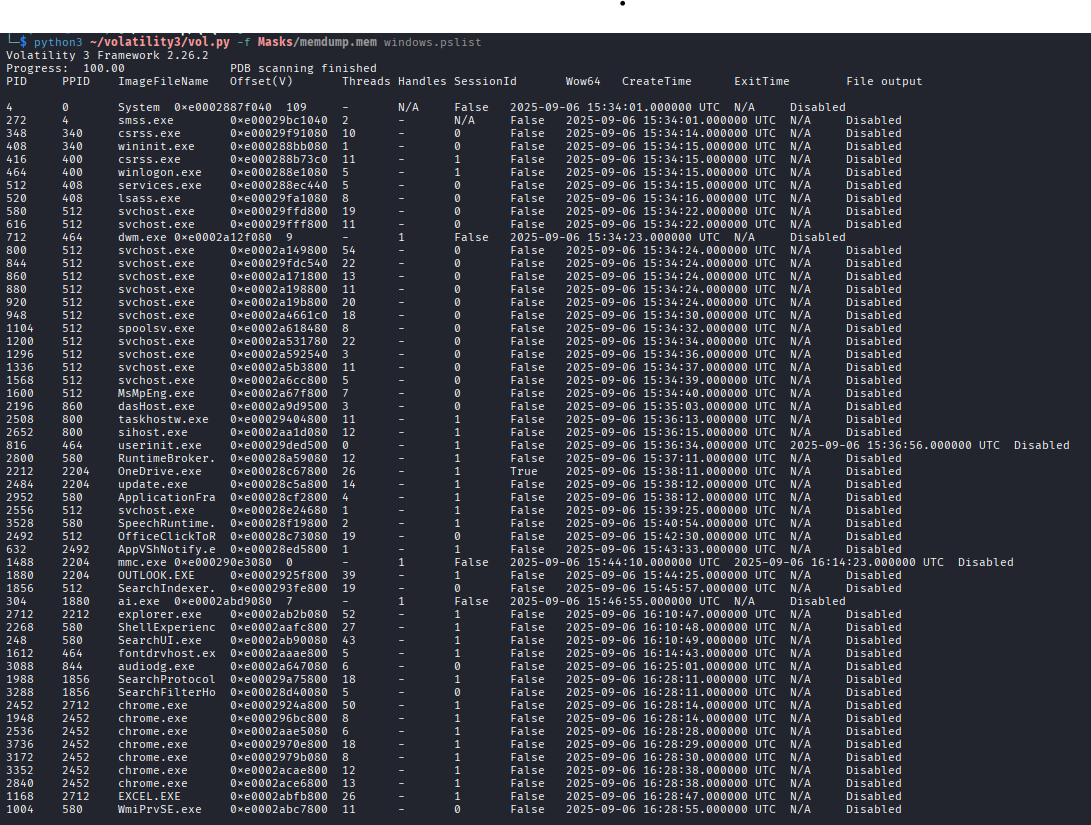
From the process list, we identify OUTLOOK.exe, which is Microsoft Outlook - the email client responsible for handling emails. Given that the challenge description mentions a phishing incident, this is clearly the process that delivered the malicious attachment.
OUTLOOK.exe
Question 2: Phishing Email Reception Time
Question: At what time was the phishing email received?
To find when the phishing email was received, we need to extract and examine Outlook's data files (OST files - Offline Storage Table).
Step 1: Enumerate Files
we list all ost files present in the memory dump
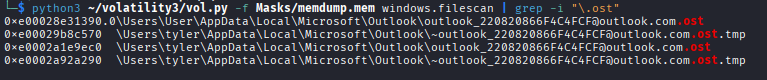
Step 3: Dump the OST File
Using the offset obtained from filescan, we dump the OST file:
Step 4: Export OST Contents with pffexport
We use pffexport to extract the contents of the OST file:
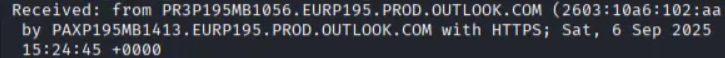
After exporting, we examine the exported files and locate the timestamp showing when the malicious email was received.
Question 3: CVE Identification
Question: What CVE was exploited by the malicious attachment?
From the exported OST contents, we found a suspicious .rar attachment. Let's analyze it.
Extract Strings from the RAR File
Examining the strings output revealed a path to a suspicious .exe file which appears to be the malicious loader.
Hash Analysis with VirusTotal
Calculate the hash and check it on VirusTotal:
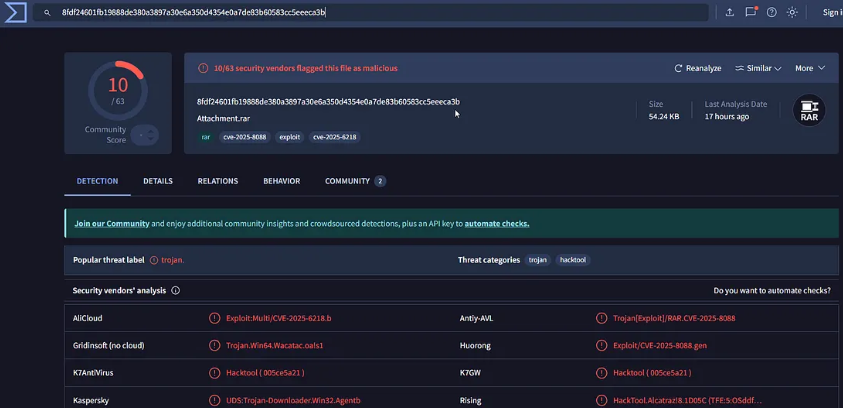
VirusTotal confirms the file is malicious and provides information about the CVE being exploited. Cross-referencing with Google searches for the loader path also reveals the CVE.
Question 4: Malicious Loader Path
Question: What is the full path of the malicious loader executable?
From Question 3's strings analysis of the RAR attachment, we already discovered the full path to the malicious loader.
Question 5: Malicious Loader Hash (The Tricky One!)
Question: What is the SHA256 hash of the malicious loader?
❌ First Attempt (Failed)
Search for the loader file in files.txt, dump it, and calculate SHA256:
✅ The Solution: AmCache Analysis
The AmCache.hve is a Windows registry hive that stores detailed information about programs that have been executed or installed on a system. It's extremely valuable in digital forensics for tracking program execution and identifying malware.
Important: AmCache stores SHA1 hashes of executed programs, which can be cross-referenced with VirusTotal to get the SHA256 hash.
Volatility 3 has a plugin called windows.amcache that extracts this information:
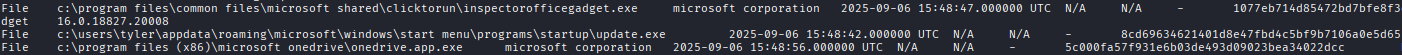
This outputs all executed programs with their SHA1 hashes. We locate our malicious loader and get its SHA1 hash.
Cross-Reference with VirusTotal
Search VirusTotal with the SHA1 hash to obtain the complete file information, including the SHA256 hash.
Question 6: Shellcode URL
Question: What is the URL from which the shellcode was downloaded?
With the malicious loader's hash identified, we can use VirusTotal's Behavior tab to see the malware's dynamic analysis results.
VirusTotal Behavior Analysis
Navigate to the Behavior tab on VirusTotal for the loader's hash. This shows:
- Network connections and DNS requests
- File operations
- Registry modifications
- Downloaded or dropped files
In the network activity section, we find the URL from which the malware downloaded its shellcode payload.
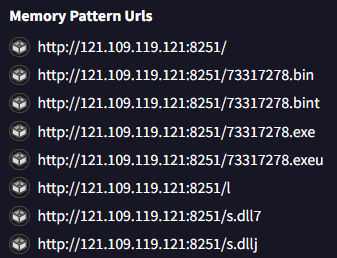
Question 7: Command & Control Server
Question: What is the C2 (Command and Control) IP address and port?
The malicious loader spawned a process called update.exe (PID: 2484). To find the C2 server, we need to analyze this process's memory.
Step 1: Dump Process Memory
Step 2: Extract Strings
Step 3: Search for Network Indicators
Searching through the strings file for IP addresses, we identify the C2 IP address
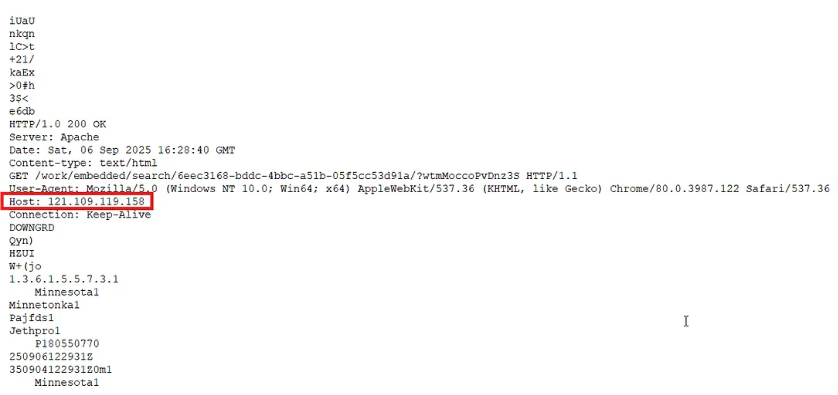
For the port, we found a port scanning command that referenced three potential ports. Testing these ports revealed which one was the active C2 port.
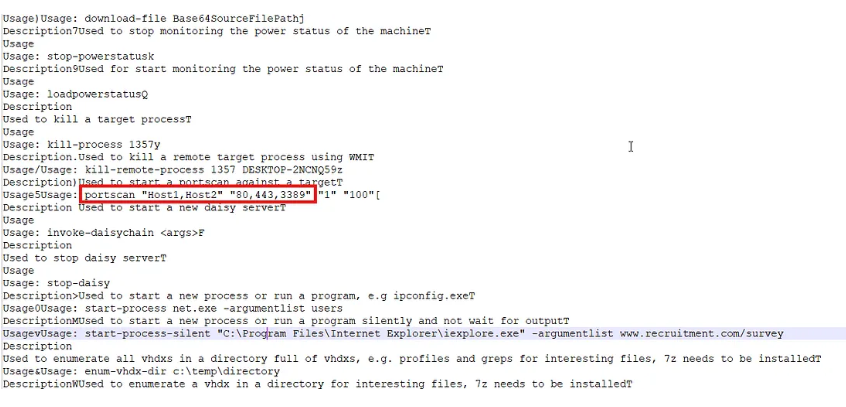
Note: This might be an unintended solution, but it worked! 😝
Question 8: Persistence Mechanism
Question: What command did the attacker use for persistence?
❌ Initial Attempts
1. Process Memory Search: Searched update.exe memory for PowerShell commands - no persistence found.
2. Traditional Registry Keys: Checked common persistence locations:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
Result: No malicious entries found!
✅ The Breakthrough: Scheduled Tasks
After hours of searching, we pivoted to examining Windows Scheduled Tasks - a common but often overlooked persistence technique. Scheduled tasks are stored as XML files in
C:\Windows\System32\Tasks.
Step 1: Search for Task Files
Search files.txt for entries in the Tasks directory:
Step 2: Identify Suspicious Task
We found a suspicious scheduled task named MicrosoftUpdate. This is suspicious because:
- It mimics legitimate Windows Update naming (social engineering)
- The context involves a loader named "update.exe"
- Legitimate Microsoft tasks have different naming patterns
Step 3: Dump and Analyze
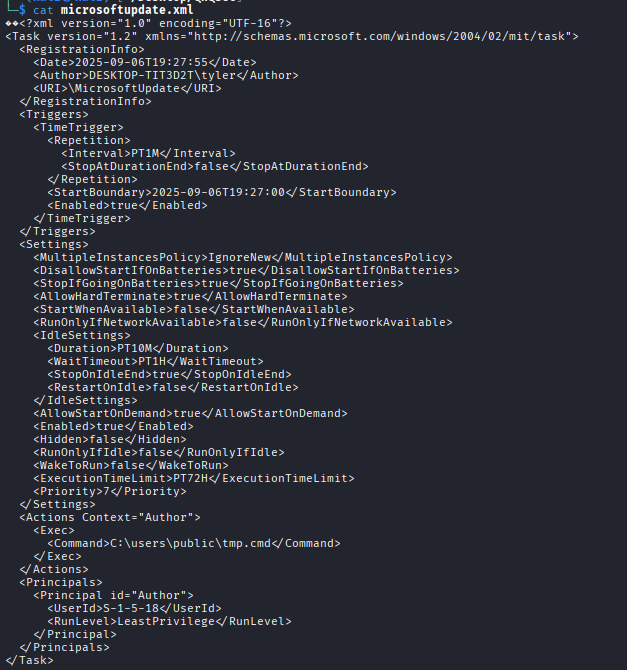
Reading the XML contents, we find the <Command> element containing the persistence command.
Challenge Complete! 🎉
Investigation Summary
8
Questions Solved
5+
Volatility Plugins
AmCache
Key Artifact
Scheduled Task
Persistence Method
Key Takeaways
- Memory forensics is multi-layered: Different artifacts (process memory, registry hives, scheduled tasks) provide different pieces of the puzzle.
- AmCache is invaluable: When direct file extraction fails, Windows artifacts like AmCache can provide the hashes needed for further investigation.
- VirusTotal enhances analysis: Cross-referencing hashes with threat intelligence platforms accelerates investigation and provides behavioral insights.
- Think beyond common persistence: Attackers increasingly use scheduled tasks instead of traditional Run keys.
- Context matters: Names like "MicrosoftUpdate" and "update.exe" provide clues when analyzed in context.
Tools & Techniques
Memory Forensics
- Volatility 3
- windows.pslist
- windows.filescan
- windows.dumpfiles
- windows.memmap
- windows.amcache
Email Forensics
- pffexport
- OST/PST Analysis
Malware Analysis
- VirusTotal
- Hash Analysis
- Behavior Analysis
- strings utility
Persistence Analysis
- Registry Analysis
- Scheduled Tasks
- Windows Artifacts
Explore More Challenges
Check out other forensics writeups from QnQSec CTF 2025.